How to design an Access Control system
CIE’s professional system designers have put together a detailed list of professional tips and questions to ask to help you specify and design a door entry or access system which will meet the individual needs of your project, client and residents or work force.
How to design an Access Control system
Access Control comes in many different forms; from door intercom systems, to gate & barrier access to the latest in smart locks and remote unlocking from your smart phone.
In specifying and designing the most suitable access control or door entry system for your building, there are a number of key factors to consider, in order to achieve the most effective and secure results.
CIE’s professional system designers have put together a detailed list of professional tips and questions to ask to help you specify and design a door entry or access system which will meet the individual needs of your project, client and residents or work force.
Top 17 Tips for Access Control system design
1. Scale of project and future expansion
The scale of an access control / door intercom project includes a number of different considerations, both in terms of size of property / campus and number of end point devices required.
The scale of project not only affects budget, of course, but also the choice and functionality of access control devices, cabling infrastructure and the ability to expand the system as the project / site expands or connects with additional sites.
2. Number of users requiring access
The scale and application of the project will have a significant influence on the number of users who will be requiring access to the building. Lower user numbers may allow for more secure authentication methods; whereas high foot traffic and a need for fast throughput may require simple, high speed authentication methods and high speed door/barrier opening and closing.
The type of users will also affect the choice of system; are users all regular, registered individuals (eg. residents or staff) or are there a high number of unregistered visitors needing access to and from the building?
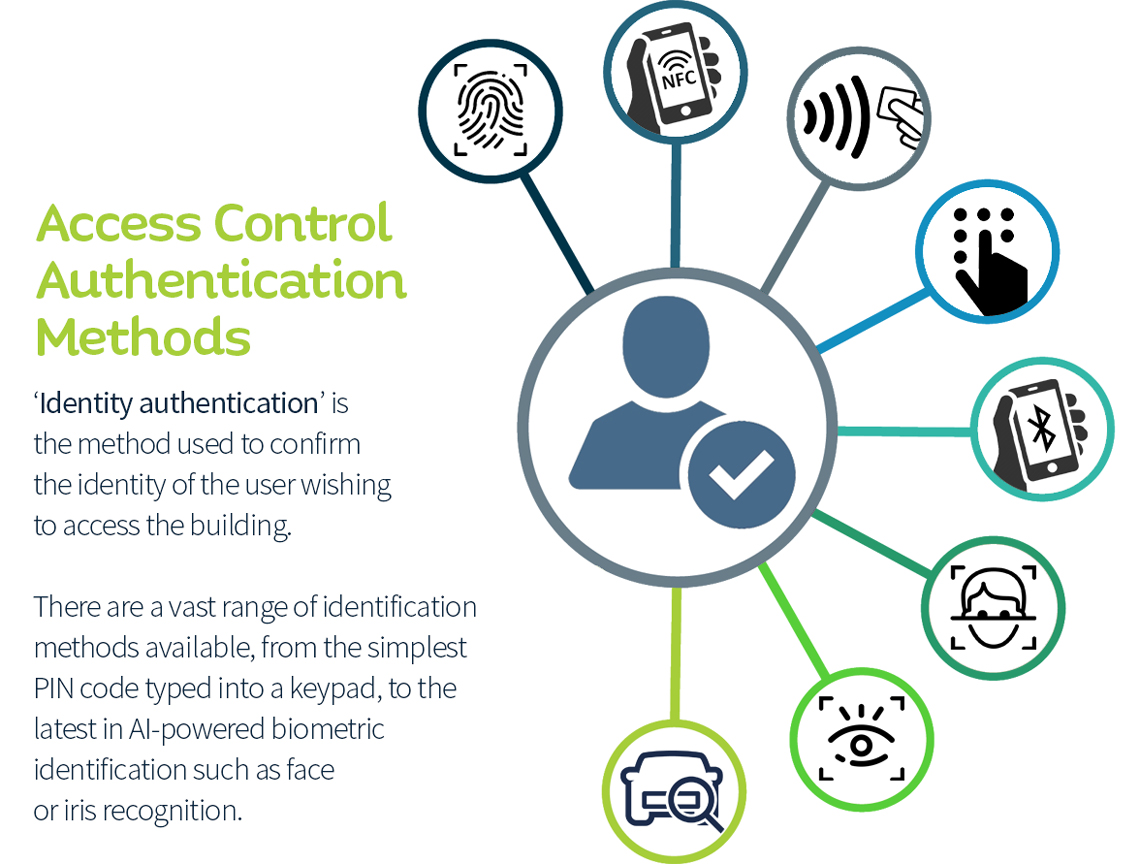
3. What sort of identity authentication is required?
‘Identity authentication’ is the method used to confirm the identity of the user wishing to access the building. There are a vast range of identification methods available, from the simplest PIN code typed into a keypad, to the latest in AI-powered biometric identification such as face or iris recognition.
Identity authentication methods:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
4. Multiple-factor Authentication methods or multiple options?
Higher levels of access security can be achieved using multiple-factor authentication (sometimes referred to as dual-authentication), where a combination of two or more identity verification methods is required to allow entry. For instance, a system may require the user to scan their smart phone for Bluetooth or NFC and enter a unique PIN or password into the access unit’s key pad.
Multiple-factor authentication should not be confused with multiple authentication methods; many door intercom and access control devices will feature a variety of identity verification options to choose from, whilst only requiring the user to provide one identifier for entry – eg. Bluetooth or NFC or PIN code).
5. How many access location points in the system and how will they be used?
Large scale projects may have high numbers of access locations for staff, visitors and vehicle access. Undertaking a detailed site review to confirm all access (entry and exit) points – including external and internal locked doors, gates, barriers, car park access and secured separate buildings – is essential in calculating the correct quantity and functionality of access or door intercom end points.
6. Does every door or gate require access control?
Be sure that all of the doors and gates you have identified for access control really do need a locking mechanism and access control. Consider whether or not access control is essential to each individual door or are there certain entrances/exits where it would be a hindrance?
For example, in high foot traffic areas, the need for each individual user to pause to authenticate their identity is likely to slow down the flow of movement; can the number of controlled access points in the route through the building be reduced?
And are secure locked doors required for all of the identified areas? Do the WCs or bin stores, for example, require access control?..
7. Internal or external access points?
The location of access control or door intercom devices will dictate the choice of devices, particularly outdoor or harsh environments. Professional access control and door intercom brands will offer both IP (ingress protection) and IK (impact protection) ratings for weather, vandal and harsh condition resistance. (The higher the IP and IK rating, the greater the level of protection).
In addition, consideration of light and temperature changes should also be considered, particularly in outdoor locations. Many door intercom systems will feature built-in cameras for the resident or security officer (for example) to visually identify visitors from a remote location. Low light levels at night time and glare (eg. due to the position of the sun) can greatly affect the picture quality. However, many high quality intercom devices will feature low light cameras or infrared lights to give high performance picture quality at night.
Due to the coronavirus pandemic, body temperature detection has become increasingly common in access control and intercom devices to help identify fever-like symptoms and reduce the spread of the virus among staff or residents. However, the accuracy of thermal detection systems can be notably affected by outdoor ambient temperatures and, therefore, are recommended for indoor location for the most successful results.
8. Does the access point require audio / video communication? (Access Device or Door Intercom)
A standard ‘access control’ point does not require any interaction / communication with another person in order to authenticate identity and, therefore, gain access. However, where unexpected visitors require access and are, in effect, ‘ringing the doorbell’ – communication with an individual apartment resident or reception/security office staff, in the case of commercial premises, requires audio / and or video communication. And in simple terms, this is the difference between an access control device and a door intercom device; the ability to communicate via video and/or audio.
Therefore, if audio/ video communication is a requirement, then a door intercom device will be required. A huge variety of intercom devices are available on the market with a wide range of functionality and authentication methods. But for communication purposes, specifying a device / system with built-in microphones and/or camera is required.
In such cases, of course, an ‘answering device’ for the resident / staff is also required, which will usually take the form of a telephone, videophone or answering panel. (And increasingly, remote answering and access via smart phone is becoming a standard option for IP intercom and access systems).
9. What type of lock technology will be required?
There are various types of Door / Gate locking methods available dependent upon the levels of security required, functionality and application of the system.
Electric or electronic lock systems are used in conjunction with an access control or door intercom device, with the access/intercom sending a signal to the lock once identity authentication has been confirmed.
-
Maglock (Magnetic Lock)
A maglock is a strong electromagnet normally located above a door. It's attracted to a door plate when powered holding the door locked. The door is unlocked by the opening of a relay which cuts power to the lock.
-
Electric Strike Lock
A strike is a device that lives in the door frame in line with the catch. It goes 'slack' when powered to allow the latch to 'pull through' the strike and the door to open in the case of a fail secure strike and goes slack when not powered in the case of a fail-safe (same as a maglock).
-
Solenoid Lock
A Solenoid is a bolt-like device that moves in a particular direction when electrically-powered. A maglock, strike and solenoid all rely on electromagnets to operate.
-
Automatic Gate Controller
A device that tells a gate motor to operate when it receives a signal. In the case of an intercom this signal would normally be a closing contact from a relay in the form of a pulse which momentarily completes a circuit.
10. How to exit the building? (Egress options)
What (or who!) goes in, must come back out! So as well as considering access into the building, consider the form of egress (exit) on each door or access point. In most cases the level of security to exit will be lower than that for access into the building.
- So exiting may simply require a manual, mechanical egress option such as a door handle or push bar.
- It may require 2nd-party interaction such as a request-to-exit ‘buzzer’ or intercom button, advising concierge or the security office, from which the door unlock can be activated remotely.
- Automated ‘RTE’ (Request to Exit) buttons can be physical (Press to Exit) or contactless in the form of a ‘no-touch button’ featuring an infrared sensor.
- Or security levels may be required to be just as high for exit as it is for entry to the building, in which case a duplicate access control device may be required on both sides of the door.
11. How will the access control points be powered? (PoE or 12v power supply?)
For an IP-connected access system (a system connected via internet protocol using standard LAN infrastructure), most IP access control, door intercom and door answering devices will support PoE (Power-over-Ethernet), therefore using the same Category cable for both data and power connectivity. POE is normally supplied from a suitable network switch or PoE injector.
Most access and door intercom devices can also be powered via external 12v power supply, either as an alternative or as a back-up supply to the PoE, should there be a network outage for any reason.
12. What happens in the event of a power cut?
Though power cuts are a rare occurrence these days – and many buildings feature backup power supplies such as generators or UPS (uninterruptible power supplies) – it is still a fire and safety requirement of access control system designs to consider access to and from the building in the case of a power outage.
So consider each lockable access point and whether to apply Fail Safe control (the door or gate automatically opens in a power outage) or Fail Secure control (the door or gate remains locked in a power outage). Please consult access control and fire safety regulations for where and when to apply fail safe and fail secure locking methods
13. Flush or surface mount devices?
Most access units and door intercom devices can be supplied with a choice of flush-mount or surface-mount back boxes or mounting plates. Surface mounting of devices is quicker and easier as there is no requirement to cut a hole in the wall for the back box; simply fix directly onto the wall. However, flush mounted devices may be preferable both aesthetically and for protection purposes (both from being damaged and from adverse weather conditions.
Choosing which mounting format involves a number of parameters including:
-
Wall/surface material the devices will be mounted on or into
If the devices are being located inside, then the materials the wall is made from are likely to be more accommodating for flush mounting (eg. plasterboard). Some building materials will be very difficult to cut into for a back box, in which case, surface mounting of the device is required.
-
Ease of installation
Surface mount installation will inevitably be quicker and easier than flush mount, as there is no requirement for cutting a hole for pattress back boxes.
-
Depth of wall
Limited thickness of wall may make it difficult or impossible to flush mount a device.
-
Protection against damage and the elements
Flush mounting of devices can often provide greater protection from damage (the device is not protruding from the wall and is less susceptible to being caught) and from water / rain ingress.
14. Door logging – how should door activity be logged?
Is there a requirement for logging of door activity? (ie. Who has accessed and exited the building, when and how frequently). This might be required for health & safety or fire regulations, or perhaps for integration with staff attendance systems.
Consider how this data should be stored and who has access to this information. The door activity data may be stored on an on-site server or can be stored in the cloud via the IP access/intercom system’s management software platform.
15. Integration with lift access control?
Are there lifts (elevators) in the building and is identity authentication required to use them? For instance, in a shared office environment, users may only have access to specific office floors of the building. In an MDU / multi-floor apartment application, resident lift access may be restricted to the floor of their apartment and all-resident areas such as gymnasium, pool, lobby etc.
In such cases, not only can access control be integrated, but also ‘lift call’ can be an added functionality, for example from each individual apartment door answering panel.
16. Is remote monitoring or emergency alarm integration required?
In order to support independent living in MDU residential buildings and retirement villages, smart home answering panels can be integrated with telecare remote monitoring and emergency alarm call systems.
Emergency telecare buttons (such as pendant or wristband buttons) can be programmed to connect to the intercom answering panel to either unlock the door or call an emergency phone number for assistance.
17. Making an access control system inclusive for impaired users
Ensuring that access systems provide inclusive use for impaired users is a legal requirement of The Equality Act. Simple design considerations such as locating access/intercom endpoints in locations accessible to all users is recommended. Additional system functionality such as voice control and integrated hearing induction loop systems will support users with limited mobility, sight or hearing impairments.
Find out more about Access Control and Door Intercoms:
Need help specifying your Access Control system?
CIE is one of the UK's leading distributors of professional access control and door intercom products from leading brands 2N and Akuvox.
Our professional system design team provide a unique system architecture service for installers and integrators to help you deliver the best in door entry and access control technology.
If you would like to discuss your next access control system or would like more information on our full range of security products, please call our team today on T. 0115 9770075 or email us now.
Featured Products